[Mac] 查詢網站支援的 SSL/TLS ciphers
今天專案有個需求,
要去確認一下友軍製作的網站,支援的 SSL/TLS ciphers 是不是夠安全。
簡單看了一下,至少有兩種方法:
1. 使用 SSL Server Test 線上服務
可以到 SSL Server Test 這個網站,
輸入想要檢測的網址,它就會對這網址做一連串的檢查,
包含網站的速度、提供的 SSL/TLS ciphers 等等,
都會列出來,是個蠻方便的線上服務~
舉例來說,下面的連結就是用它來測試一下 tw.yahoo.com 的結果:
SSL Server Test: tw.yahoo.com (Powered by Qualys SSL Labs)
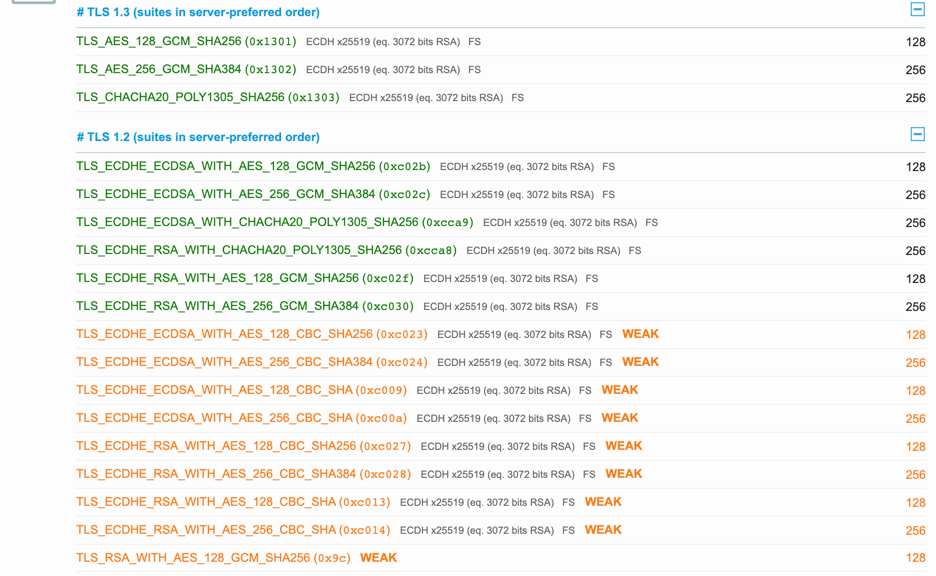
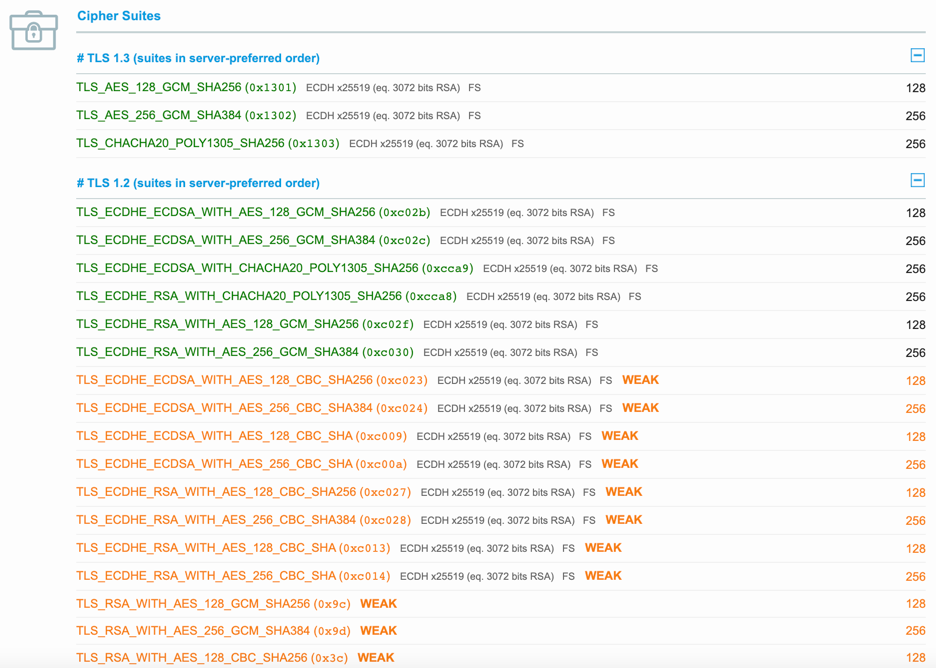
結果裡可以看到它支援的 TLS cipher suites,
而且 SSL Server Test 很貼心的把較不安全的 cipher 用 WEAK 標示出來了:
2. 使用 Nmap
Nmap 也可以用來查詢 SSL/TLS ciphers。
在 Mac 上,用 Homebrew 安裝 nmap:
brew install nmap
接著執行 nmap --script ssl-enum-ciphers -p <port> <server> ,
就可以檢測支援的 ciphers,例如:
testuser@localhost ~ $ nmap --script ssl-enum-ciphers -p 443 tw.yahoo.com Starting Nmap 7.92 ( https://nmap.org ) at 2021-09-23 19:58 CST Nmap scan report for tw.yahoo.com (202.165.107.50) Host is up (0.054s latency). Other addresses for tw.yahoo.com (not scanned): 2406:2000:e4:1605::9000 2406:2000:e4:1605::9001 202.165.107.49 PORT STATE SERVICE 443/tcp open https | ssl-enum-ciphers: | TLSv1.0: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server | TLSv1.1: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server | TLSv1.2: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A | TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A | TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server | TLSv1.3: | ciphers: | TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | cipher preference: server |_ least strength: A Nmap done: 1 IP address (1 host up) scanned in 7.25 seconds
用 nmap 查詢的話速度較快,
但就不會列出這個 cipher 是否足夠安全了~
參考資料:security – How do I list the SSL/TLS cipher suites a particular website offers?
(本頁面已被瀏覽過 2,556 次)